Stay Up to Date With Evolving Scams Like These Examples in the Manufacturing Industry
- Adriana Gutierrez, Digital Media Producer

- Sep 22, 2025
- 8 min read

This post is for informational purposes only. As much as we all despise scammers, I legally (and unfortunately) cannot share any of their personal information, as doing so would violate privacy laws. Scammers are also known for stealing identities, so innocents could be involved — just to add insult to injury. That said, I can legally roast them to help release some of our collective frustration.
Please keep in mind that scammers can “spoof” emails, making it look like they’re coming from a legitimate domain when they’re not, or it could come from a trusted source that was compromised (stolen). When in doubt, always check your email headers and do your research. (I’ll explain how to properly check headers at the end of this post.) Stay safe out there!
Zero Effort, Zero IQ, Zero Threat
We’ve all seen scam emails—starting with the timeless ‘Dear Sir/Madam,’ as if we’re about to inherit a fortune from a long-lost Nigerian uncle with a monocle and a mysterious offshore account. For our industry, this is mostly what they look like:

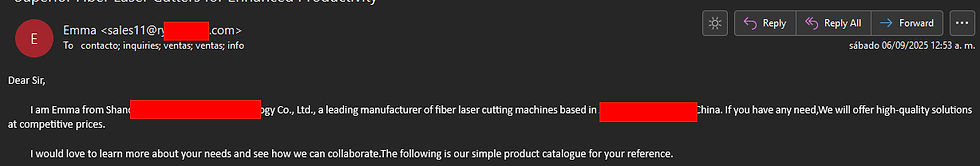
To more elaborate scams like these:

This scammer is pretending to be CFE—Mexico’s actual state-owned electric utility. You know, the one that powers millions of homes and doesn’t send shady emails from sketchy domains. The real CFE uses cfe.mx, not whatever URL this fraudster stitched together in their basement. Nice try, though. If electricity were measured in scam voltage, this one barely flickered.

The scammer’s rendition of DocuSign—now performing under the stage name ‘DocuSing.’ Because nothing says ‘secure digital agreement’ like a name that sounds like your grandma’s choir app. A+ for creativity.
Oscar-Worthy Impersonation (But Still a Scam)
This week’s scam brought a surprise: tactics that actually showed effort. I’m talking mildly convincing PDFs (they almost spellchecked!) and even a fake website. Let me start from the beginning:
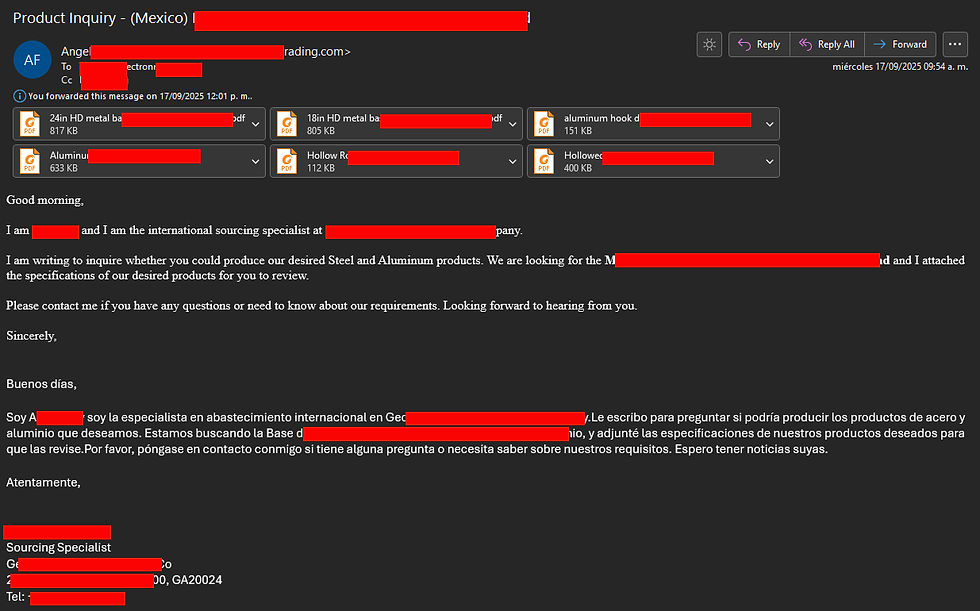
It’s not uncommon to receive bilingual emails—especially in our line of work, where we collaborate closely with clients across Mexico and the U.S, which sometimes may or may not include a few typos here and there. The moment this one hit my inbox, I forwarded it straight to our IT department (shoutout to Adrian 🙌).
While our IT team was verifying the safety of the PDFs, I conducted separate research into the company. What I found was of no surprise: the company doesn't exist. While there is an entity with a similar name, it operates in a completely different industry and is associated with a different address and website. The address used by the scammer may appear legitimate at first glance, as it is linked to an industrial building project available for lease. However, it does not correspond to any registered company name, which could mislead individuals conducting only a surface-level check.



As I did more research, I came across their website, which also had some intriguing details:
Minimal content: The site only includes vague statements like “we specialize in sourcing and importing quality raw materials” with no real product listings and team info.
Generic language: It reads like a template, not a functioning business site.
No verifiable presence: There’s no evidence of this company existing in legitimate business directories or trade registries.
Copyright date stuck at 2018: That’s often a sign of a neglected or hastily built site.
No linked social media, certifications, or client references: All typical signs of a real business are missing.
The website uses generic language, lacks real business details, and mimics a company that doesn’t exist, with only two tabs.
The domain is privacy-shielded, which is common for scammers.
It’s referenced in a suspicious email with fake invoices and packaging instructions full of typos.
The address used is tied to a rental industrial space, not a registered company.
Additionally, checking this website with tools like Scamvoid or ScamAdviser, comes back as safe. But why? While Scamvoid/ScamAdviser didn’t detect malware, that doesn’t mean the site isn’t part of a fraudulent scheme. It’s like checking if a house has termites but ignoring the fact that it’s made of cardboard. It's a barely fleshed out website meant to seem legitimate when it's just bare bones, to sell you the idea that they're trustworthy, especially if you're only conducting a quick background check.

Once I got the green light that the PDFs were safe to open, I dove in for a closer look. Now, a quick PSA: scammers love to send squeaky-clean PDFs that lull you into a false sense of security—only to sneak in a poisoned link somewhere inside, hoping you’ll click once they’ve earned a sliver of trust. But in this case? No embedded links. Just some truly entertaining content, which you'll soon see, down below:




The photos contain numerous inconsistencies and errors, which are worth reviewing closely (mainly for humor). Now, this wasn’t a one-click phishing attempt. It was a multi-step trust-building scam designed to look professional, bilingual, and industry-relevant.
Step 1: Appear Legitimate
The scammers sent clean-looking emails with no malware, no sketchy links—just well-formatted PDFs that looked like invoices or packaging instructions. That’s intentional. They want you to lower your guard.
Step 2: Build Credibility
The PDFs were mildly convincing. They used industry jargon, bilingual formatting, and even included product photos (albeit with errors). The goal? Make you think, “Maybe this is a new vendor we forgot to onboard.”
Step 3: Delay the Scam—Until You Trust Them
By not asking for money or sensitive data right away, they buy time. They want you to engage, reply, maybe even forward the email internally. That’s when they strike—often with a follow-up request for payment, wire transfer, or confidential documents.
Step 4: Exploit Surface-Level Checks
The website they linked to looked “safe” on ScamAdviser and Scamvoid. But it was just a shell—no real team, no product listings, no verifiable business presence. It’s designed to pass a quick background check, not a deep dive.
Scammers are evolving. They’re not just sending typos and fake logos anymore—they’re strategically staging legitimacy to bait professionals into trusting them. In manufacturing, where vendor onboarding is frequent and bilingual communication is common, this tactic is especially dangerous. It's funny to laugh at now but imagine a future where scammers actually put in time, effort, and money to begin structuring realistic websites, PDFs, and even AI.
Checking Headers - For Spoofing or Other Security Issues
Spoofing is when a scammer makes an email look like it’s coming from a legitimate sender—like your boss, a vendor, or even yourself. Here’s how to spot it:
1. Start with the Obvious
Check the sender’s name and email address. Look closely—scammers often use addresses that look similar to real ones (e.g., support@tectronmeta1mx.com instead of support@tectronmetalmx.com).
Look for spelling errors or strange formatting. Legitimate companies rarely send emails with typos, broken logos, or generic greetings like “Dear Customer.”
2. View the Email Headers
Email headers contain the technical routing info—like where the email actually came from. Here's how to access them (take note that these instructions may change due to future updates):
📧 Email Provider | 🔍 How to View Headers |
Gmail | Open the email → Click the three dots → “Show original” |
Outlook (Desktop) | Open email → File → Properties → Look under “Internet headers” |
Outlook.com | Open email → Three dots → “View” → “View message source” |
Yahoo! Mail | Open email → Three dots → “View raw message” |
Apple Mail | Open email → View → Message → All Headers |
Proton Mail | Open email → Three dots → “View headers” |
3. Analyze the Header Details
Once you’ve opened the headers, look for these clues:
Return-Path: Should match the sender’s domain.
Received: Shows the actual server that sent the email. If it’s not from the expected domain (e.g., microsoft.com), it’s suspicious.
SPF, DKIM, and DMARC Results: These are authentication checks. Look for:
SPF=pass
DKIM=pass
DMARC=pass
If any of these fail, the email may be spoofed.
4. Use Online Tools
You can paste the header into tools like:
Google’s Message Header Analyzer
MXToolbox Email Header Analyzer
These tools help you visualize the email’s path and spot inconsistencies.
5. Check the Domain Reputation
If the email links to a suspicious domain, run it through:
ScamAdviser
CanIPhish’s Spoofing Test
But as we've seen earlier, scammers can pass this test, however, it's still something worthwhile to check.
6. Trust Your Gut—and Your IT Team
If anything feels off, don’t click links or download attachments. Forward the email to your IT department or security team for review.
Spoofed Email Example: “Apple Support”
What the user first sees:
From: Apple Support <support@apple.com>
Subject: “Your Apple ID has been locked – Immediate Action Required”
Body Preview:
Dear Customer, We detected suspicious activity on your Apple ID. Please verify your account immediately to avoid service interruption. [Verify Now]
Visuals:
Apple logo (low-res and slightly off-center)
Button styled like Apple’s “Verify” CTA
Footer mimicking Apple’s standard legal disclaimer
At first glance, it looks legitimate. The sender name is “Apple Support,” the domain appears correct, and the message uses urgency and branding to push action.
What the user did next: Checked the headers
They opened the email and followed these steps to view the headers (in Gmail):
Clicked the three dots in the top-right corner of the email
Selected “Show original”
What they found in the headers:
Return-Path: <support@appleid-alert.com> ← Not Apple’s domain
Received: from mail.fakehost.ru (mail.fakehost.ru. [185.23.56.101]) ← Server is based in Russia, not Apple’s infrastructure
SPF: SPF=fail ← The sending server is not authorized to send on behalf of apple.com
DKIM: DKIM=fail ← The digital signature doesn’t match Apple’s domain
DMARC: DMARC=fail ← The domain’s policy was violated
Red Flags Identified
Mismatch in Return-Path: Even though the “From” field said support@apple.com, the Return-Path showed appleid-alert.com, which is not an official Apple domain.
Suspicious Sending Server: The email came from a Russian server unrelated to Apple.
Authentication Failures: All three protocols—SPF, DKIM, and DMARC—failed, confirming the email was not authorized by Apple.
What the user did next:
Did not click the “Verify Now” button
Forwarded the email to their IT/security team
Reported the domain to Apple’s phishing reporting portal

Joke's Aside - The Reality of Future Scams
While it’s easy to laugh at the typos, bizarre product names, and low-effort impersonations in scam emails, the reality is far more sobering: scammers are evolving, and AI is accelerating their game. What used to be clumsy phishing attempts are now turning into sophisticated operations.
In one real-world case, a scammer used AI to clone a man’s voice and convinced his mother-in-law that he’d been kidnapped—she stayed on the phone, withdrawing cash from multiple ATMs, all because the voice said, “Mom, just pay them. Please”. That same technology is already creeping into the manufacturing sector.
Now, imagine receiving a call from someone who sounds exactly like your company’s CEO, urgently requesting a wire transfer to a “new supplier.” Which... has actually happened—in one case, a UK manufacturer lost €220,000 after a scammer mimicked their German parent company’s executive with chilling accuracy. So yes, the roasts are fun, but the threat is real—and it’s getting smarter by the day.
Practical Anti-Fraud Tips for Manufacturers
1. Vendor Verification Protocols
Cross-check business registration: Use government databases (like SAT in Mexico or Secretary of State registries in the U.S.) to confirm the company exists.
Request official documentation: Ask for tax ID, proof of incorporation, and bank account ownership before onboarding.
Verify domain ownership: Use WHOIS tools to check when the domain was created and who owns it. Scam domains are often recently registered and privacy-shielded.
2. Multi-Channel Confirmation
Call the vendor directly: Use a verified phone number—not the one in the suspicious email—to confirm any requests.
Check with internal contacts: If the vendor was supposedly referred by someone in your company, confirm that referral through a separate channel.
3. Email Authentication Checks
Train staff to read headers: Teach teams how to spot mismatched Return-Paths, failed SPF/DKIM/DMARC results, and suspicious sending servers.
Use email filtering tools: Many companies use secure gateways that flag spoofed domains or impersonation attempts.
4. Document Integrity Review
Inspect PDFs for metadata: Check creation dates, author info, and embedded links. A clean-looking PDF might still contain hidden tracking or redirect links.
Compare formatting to known vendors: Legitimate invoices and packaging guides often follow consistent templates. Deviations can be a red flag.
5. Website and Domain Vetting
Look for real content: A legitimate site should have product listings, team bios, certifications, and client references.
Check for social media presence: Real companies usually have active LinkedIn, Facebook, or Instagram accounts tied to their domain.
6. Internal Escalation and Reporting
Create a fraud response protocol: Ensure employees know how to escalate suspicious emails to IT or compliance.
Log and share incidents: Maintain a database of scam attempts to train new staff and spot patterns.
Final Thoughts: Laugh, Learn, Stay Sharp
While it’s tempting to treat scam emails as comic relief, the truth is they’re evolving fast—and the stakes are getting higher. What starts as a typo-filled PDF or a hilariously fake invoice can quickly escalate into AI-generated voices mimicking loved ones, or spoofed emails that trick entire departments into wiring money. The humor helps us cope, but awareness helps us stay safe.
So yes, roast the scammers. Share the laughs. But also stay vigilant, educate your team, and double-check everything—because the future of scamming isn’t just annoying, it’s dangerously convincing.





